(�b�a�[�� = 0%�A�b���[�� = 100%)
100% �b���[������ήɶ��G
�ۥѿ�ܡA�I��H�U�a���[�ݿ줽�ɶ��Φ�m
�ҮɡG 30 �p��
�ɥήɴ��G 10 �P���C�i�ץѱz����A�i�֥i�C�C
�Ұ���v�ɮv�GLarry
�b�էK�O��ڻ�G�� 3 �p���A�ЭP�q�H�W�a�I�P������¾���w���C
���ҵ{�����b�էK�O��ڻ���ɮv�ѵ��A�ȡC
(�b�a�[�� = 100%�A�b���[�� = 0%)
100% �b�a�[������ήɶ��G
�C�� 24 �p�ɥ��ѭԤ������Ʀa�[��
�ҮɡG 30 �p��
�ɥήɴ��G 10 �P���C�i�ץѱz����A�i�֥i�C�C
�Ұ���v�ɮv�GLarry
�b�էK�O��ڻ�G�� 3 �p���A�ЭP�q�H�W�a�I�P������¾���w���C
���ҵ{�����ɮv�ѵ��A�ȡC
Palo Alto Networks �O�@�a���y�ʪ������w�����q�A�`��������C�Ӥ��q���ߩ� 2005 �~�A���b���ѳ̥��i�������w���N�A���U�Ȥ�O�@����������c�N�n��B���������M��ƥ~�����I�`�C
Palo Alto Networks �}�o�M���Ѥ@�t�C�����w���ѨM��סA�]�A�U�@�N������ (Next Generation Firewall)�B���ݦw�� (Prisma Cloud)�B�����w�����R (Cortex XDR) �M���I�O�@ (Endpoint Protection)���C
�o�ǸѨM��׳����ۥD��o���N�A�p�w���W�h (Security Policy)�B�¯ٱ��� (Threat Intelligence)�M�۰ʤƦw����� (Cortex XSOAR)�A�H�T�O�Ȥ᪺�����w���C
Palo Alto Networks ���Ȥ�]�A���y�d�����~�B�F�����c�B�Ш|���c�M�A�ȴ��Ѱӵ��C
Palo Alto Networks �b���y�֦��h�Ӭ�o���ߩM��ƳB�A���ΤF�Ƥd�W���u�A�O�����w����~���T�j��ɪ̤��@�A�Ԩ��H�U Gartner - Magic Quadrant for Network Firewalls:
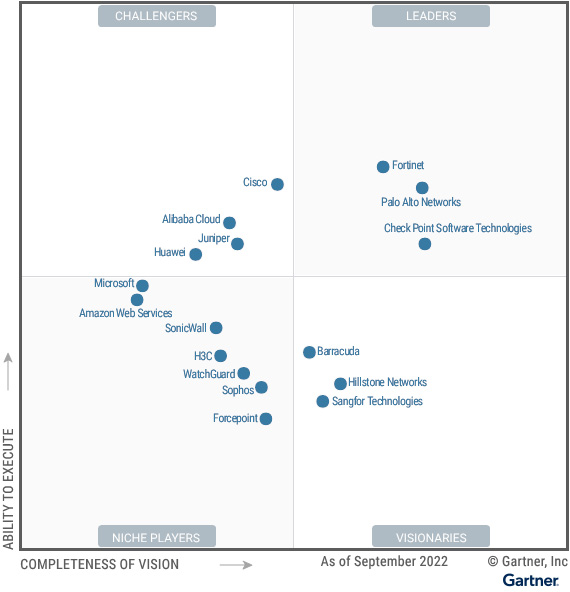
�@���@�a�P�O������w�������q�APalo Alto Networks �`�����ʺ����w�����зs�M�o�i�A�P�~����L���q�M��´�X�@�A�@�P���藍�_�X�{�������¯١C
Palo Alto Networks �����Ȭ��� 1250 ������ (�W�L 9750 ���䤸)�A�Ӥ��q�ѻ���� 5 �~�e�� 24 �����r�ɦܲ{�b�� 200 �����A�O���y�����w����~��������~���@�C
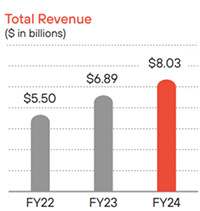
�ھڸӤ��q���~�װ]���ƾ���ܡA����~�禬�� 80 �������A���W�~�P���W�� 16.5%�F��Q���� 59 �������C
Palo Alto Networks �b�����w�����������۷��j���������B�A�S�O�O�b�U�@�N������ (Next Generation Firewall) �M�����w�����R�������{�u���C
�ڥ�����s���c IDC �̪��i��ܡG
- Palo Alto Networks �b <<���y�����𥫳����B>> �ƦW�Ĥ@�A���������v�� 22.4%�F
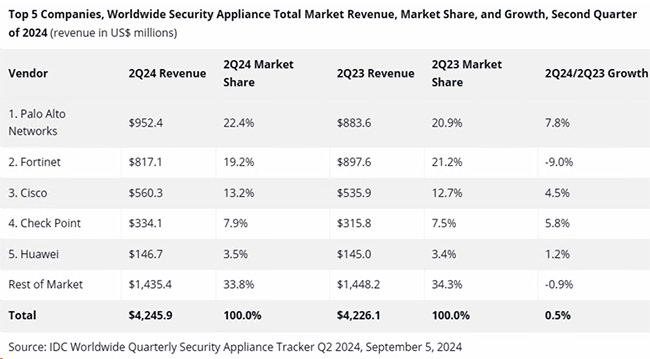
�`��Ө��APalo Alto Networks �b�����w����~�֦�í�����]�Ȫ��p�M�j�j�������a��A�ë���q�L�N�зs�M�~�ȩݮi�ӱ��ʨ�b���������v���O�C
Palo Alto Networks ���֤ߧN�GPAN-OS (���ҵ{���D�n���e)
PAN-OS ���M�εw�� (�]�A PA �t�C Next Generation Firewall) �M�����ƥ��x (�]�A VM �t�C�� CN �t�C)�A���ѤF�@�t�C�����w���ѨM��סA�]�A�U�@�N������B���ݦw���B�����w�����R�M���I�O�@���CPAN-OS �֦��@�t�C���i���\��A�]�A�G
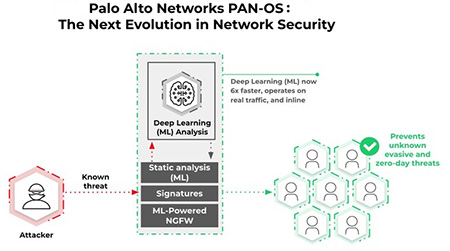
- ���ਾ����G�Q�β`�Dz� (Machine Learning powered) �M�H�u���z (Artificial Intelligence) �N�A������y�q�i���ɤ��R�M���ѡA�ï���۰ʾDzߩM�վ㨾����W�h�C
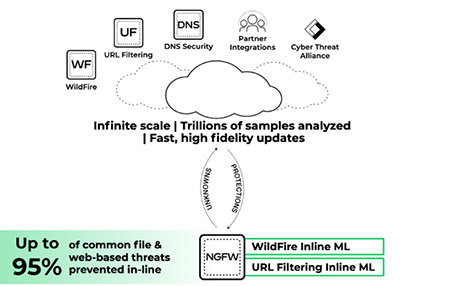
- �w�����R�GPalo Alto WildFire �N�j�q�������w���ƾڶi�榬���M���R�A�H�K�ήɵo�{�M����U�ث¯١A�]�A�c�N�n��B���������M��ƥ~�����C
- �������q�G�q�L���κ����y�q�A�ϱo�U�ӳ����ΥΤᤧ�����y�q���۹j���A�H��֫¯٪��X���M���I���Ǽ��C

- �۰ʤƦw������G�q�L�۰ʤƧN�A�i�H�۰ʤư���w���ާ@�A�p��������y�q�B�j���P�V�D���M�����ƥ~�����C
Palo Alto Networks PA/VM/CN �t�C������O�������M�۰ʤƪ��N�A�i�H���Ħa�����������U�ئy�ݪ��¯١A�p�f�r�B�c�N�n�C
��o Palo Alto Networks Certified Next-Generation Firewall Engineer �{�Ҫ��H�h�A�i�ܤF�L�̨�Ʀ��ާ@ Palo Alto Networks �U�@�N������ӫO�@�����K���y�ݺ����¯٪���O�C
| �ҵ{�W�١G |
Palo Alto Networks Certified Next-Generation Firewall Engineer ��ڻ{�i�Үѽҵ{ - ²�١GPalo Alto Networks Firewall Training Course (���� 7x24 ��߾���) |
| �ҵ{�ɼơG | �X�@ 30 �p�� (�@ 10 ��) |
| �A�X�H�h�G | ��q�������w�����{�ѩΦ��ӧ먭 I.T. �ɪ��H�h |
| �½һy���G | �H�s�F�ܬ��D�A���H�^�y |
| �ҵ{���O�G | �����߾ɮv�˦۽s�g�^�嬰�D���O�A�ӳ����^��r���������ӡC |
�u�n�A��U�C��ب��o�X�榨�Z�A�K�i�� Palo Alto �{�o Palo Alto Networks Certified Next-Generation Firewall Engineer ��ڻ{�i�ҮѡG
|
�����߬� Palo Alto Networks ���w�� NGFW-Engineer �Ҹոճ��A���ҮɽЭP�q�����ߡA�n�O�����Ҥ���ئҸսs�� (�Y NGFW-Engineer)�B�Ҹդ���ήɶ� (�̧֥i�Y�����)�C�{�Ҹիe�n�X�ܨ����Ҥ�ú�I�ҸնO HK$2,050�C �Ҹ��D�إѿD�w�Ҹդ��߶ǰe��A�n���Ҫ��q���A�ҸծɥH�q���@���C�Ҧ��Ҹ��D�ا����^��A�Ӥj�h�ƪ��Ҹ��D�ج��涵����D (�N�Y O) �Φh������D (�N�Y �f)�C�@��������|�ߧY�X�{�A�����ơA���G�Y�ҧY���I�Ҹդ��X��K�i���s���ҡA�������ơC�����D�@���ɶ��B�D���`�ơB�X����Ƶ��ԲӦҸո�ơA�i�s�������ߺ��� "�U��Ҹդ��Ƹ��"�C |
| �ҵ{�W�١GPalo Alto Networks Certified Next-Generation Firewall Engineer ��ڻ{�i�Үѽҵ{ - ²�١GPalo Alto Networks Firewall Training Course (���� 7x24 ��߾���) |
1. Device Management and Services
1.1 Firewall Management Interfaces
1.1.1 Management interfaces
1.1.2 Methods of access
1.1.3 Web interface
1.1.4 Panorama
1.1.5 XML API
1.1.6 Access restrictions
1.2 Introduction to PANOS
1.2.1 App-ID
1.2.2 Content-ID
1.2.3 Device-ID
1.2.4 User-ID
1.2.5 WildFire Inline ML
1.3 Deploying the VM-Series Firewall
1.3.1 VM-Series Models
1.3.2 Supported Deployments on VMware vSphere
1.3.3 VM-Series on VMware System Requirements and Limitations
1.3.4 Plan the Interfaces for the VM-Series for ESXi
1.3.5 Deploying the OVA for practice
1.3.6 Perform Initial Configuration on the VM-Series on ESXi
1.4 Licensing
1.4.1 License Types
1.4.2 Flexible vCPUs and Fixed Model Licensing
1.4.3 Flexible vCPUs and Fixed Model Deployment
1.4.4 When licenses expire
1.5 Deploying Palo Alto VM-Series Next Generation Firewall on Clouds
1.5.1 About the VM-Series Firewall on Azure
1.5.2 Azure Networking and VM-Series Firewall
1.5.3 VM-Series Firewall Templates on Azure Cloud
1.5.4 Deployments scenarios supported on Azure Cloud
1.5.5 Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
2. Network Segmentation with Interfaces and Zones
2.1 Designing Network Segmentation for a Reduced Attack Surface
2.1.1 Background
2.2 Configure Interfaces and Zones
2.3 Configure a Basic Security Policy between Zones
2.3.1 Background information and General concepts of Security Policy
2.3.2 Detailed Firewall Packet processing flow
2.4 Assessing Network Traffic
2.5 Service Route
3. Firewall Administration
3.1 Understanding the Candidate Configuration
3.2 Save and Export Firewall Configurations
3.2.1 Saving a local backup
3.2.2 Exporting Configurations
3.3 Restoring and Reverting Firewall Configuration
3.3.1 Revert to the current running configuration (file named running-config.xml).
3.3.2 Revert to a previous version of the running configuration that is stored on the firewall
3.3.3 Revert to Custom-named candidate configuration snapshot
3.3.4 Revert to a running or candidate configuration that you previously exported to an external host
4. Administrative Accounts
4.1 Administrative Role Types
4.1.1 Role Based
4.1.2 Dynamic
4.2 Configuring Admin Role Profile
4.3 Inside an Admin Role Profile Construction
4.4 Create and Configure Firewall Administrator Account
4.5 Configure Tracking of Administrator Activity
5. Zone Protection and DoS Protection
5.1 Packet Buffer Protection
5.1.1 Global Packet Buffer Protection
5.1.2 Per-Zone Packet Buffer Protection
5.1.3 Packet Buffer Protection Based on Buffer Utilization
5.2 Zone Attacks
5.3 Zone Defense Tools
5.3.1 Zone Protection profiles
5.3.2 DoS Protection profiles and policy rules
5.3.3 Summary
5.3.4 Firewall Placement for DoS Protection
5.4 Configuring and Applying a Zone Protection Profile
5.4.1 Flood protection in Zone Protection profile
5.4.2 Reconnaissance Protection in Zone Protection profile
5.4.3 Packet-Based Attack Protection
5.4.4 Protocol Protection
5.4.5 Ethernet SGT Protection
5.4.6 L3 & L4 Header Inspection
5.4.7 Configure Email notification for Alerts
5.5 DoS Protection Profiles and Policy Rules
6. App-ID
6.1 Introduction to App-ID
6.2 Streamlined App-ID Policy Rules
6.2.1 Create an Application Filter Using Tags
6.2.2 Background information about Decryption and APP-ID policy inspection
6.2.3 Keys and Certificates for Decryption Policies
6.2.4 Configuring SSL Decryption with SSL Forward Proxy
6.2.5 Creating a Decryption Policy rule
6.2.6 Verify Decryption
6.3 Decryption Exclusions
6.3.1 Reasons to Exclude Web sites from being decrypted by PA firewall
6.3.2 Palo Alto Networks Predefined Decryption Exclusions
6.3.3 Exclude a Web Site from Decryption for Technical Reasons
6.3.4 Exclude a Web Site from Decryption for Compliance and Privacy Reasons
6.3.5 Temporarily Disable SSL Decryption
6.3.6 Decryption Log
7. Security Profiles
7.1 Antivirus Profile
7.2 Anti-Spyware profiles
7.2.1 Default profile
7.2.2 Strict profile
7.3 Vulnerability Protection profiles
7.4 URL Filtering Profiles
7.5 Data Filtering Profiles
7.5.1 Creating a Data Filtering Profile
7.6 File Blocking Profiles
7.6.1 Basic file blocking
7.6.2 Strict file blocking
8. External Dynamic List
8.1 Introduction to External Dynamic List
8.2 EDL Types
8.2.1 Predefined IP Address
8.2.2 Predefined URL List
8.2.3 IP Address
8.2.4 Domain
8.2.5 URL
8.2.6 Equipment Identity
8.2.7 Subscriber Identity
8.3 EDL Formatting
8.3.1 IP Address List
8.3.2 Domain List
8.4 Built-in External Dynamic Lists
8.4.1 Palo Alto Networks Bulletproof IP Addresses
8.4.2 Palo Alto Networks High-Risk IP Addresses
8.4.3 Palo Alto Networks Known Malicious IP Addresses
8.4.4 Palo Alto Networks Tor Exit IP Addresses
8.5 Configure the Firewall to Access an External Dynamic List
8.6 Enforce Policy on an External Dynamic List
8.7 Retrieve an External Dynamic List from the Web Server
8.8 Using EDL Hosting Service feeds
9. Advanced WildFire
9.1 Introduction
9.2 Available subscription options
9.2.1 WildFire
9.2.2 Advanced WildFire
9.2.3 Standalone WildFire API
9.3 WildFire Features
9.3.1 Real-Time Updates
9.3.2 Five-Minute Updates (All PAN-OS versions)
9.3.3 Advanced WildFire Inline ML�X(PAN-OS 10.0 and later)
9.3.4 File Type Support
9.3.5 Advanced WildFire API
9.3.6 WildFire Private and Hybrid Cloud Support
9.3.7 Intelligent Run-time Memory Analysis
9.4 Advanced WildFire Concepts
9.4.1 Samples
9.4.2 Firewall Forwarding
9.4.3 Advanced WildFire Analysis Environment
9.4.4 Advanced WildFire Inline ML
9.4.5 Advanced WildFire Verdicts
10. Managing Policy Objects
10.1 Address and Address Group Objects
10.1.1 How to tag objects
10.1.2 Address Object
10.1.3 Address Group object
10.2 Services
10.3 Application Filters
10.4 Application groups
10.5 Nesting application groups and filters
10.6 Application Characteristics
10.7 Policy Design and Evaluation
10.7.1 Create Security Policy Rules by App-ID instead of by Service
10.7.2 Rule Shadowing
10.7.3 Policy Usage statistics
10.7.4 Security Policy Rule Logging options
10.7.5 A Brief description of User-ID
10.7.6 Policy test match tool
10.7.7 Traffic Logging with Tap zone interface
10.7.8 Virtual Wire Interface
10.8 Layer2 vs Layer3 Interfaces
10.9 Sub-Interfaces
10.9.1 VLAN tags in conjunction with IP classifiers (address, range, or subnet).
10.10 Tunnel Interface
10.11 Aggregate interfaces
11. High Availability
11.1 Palo Alto HA Overview
11.2 HA Modes
11.2.1 Active/Passive
11.2.2 Active/Active
11.3 Failover Triggers
11.3.1 Heartbeat Polling and Hello messages
11.3.2 Link Monitoring
11.3.3 Path Monitoring
11.4 Floating IP Address and Virtual MAC Address
11.5 ARP Load-Sharing
11.6 Route-Based Redundancy
11.7 Firewall Session Owner
11.8 Firewall Session Setup
11.8.1 Session Setup Option
11.9 Prerequisites for Active/Passive HA
11.10 Configure Active/Passive HA
11.11 Verify Failover
12. Security in Quantum Computing Era
12.1 Quantum Security Concepts
12.2 Quantum Computing Threat
12.2.1 What Is A Quantum Computer?
12.2.2 How Does the Quantum Threat Affect My Network?
12.2.3 What to Do Now to Mitigate Harvesting Attacks
12.3 How RFC 8784 Resists Quantum Computing Threats
12.4 Support for Post-Quantum Features
12.4.1 RFCs Supported and Interoperability
12.4.2 HA Support
12.4.3 Upgrade and Downgrade Considerations
12.5 Post-Quantum Migration Planning and Preparation
12.5.1 Assign Resources and Build Awareness
12.5.2 Define Responsibilities
12.5.3 Develop a Crypto Inventory and Priority List
12.5.4 Evaluate Solutions, Experiment, and Test
12.5.5 Continue to Monitor Progress
12.6 VPN Configuration Best Practices
12.6.1 RFC 8784 Best Practices
12.6.2 RFC 9242 and RFC 9370 Best Practices
12.7 Configure Post-Quantum IKEv2 VPNs with RFC 9242 and RFC 9370 Hybrid Keys
13. GlobalProtect
13.1 Overview of GlobalProtect
13.2 Components of GlobalProtect
13.2.1 GlobalProtect Portal
13.2.2 GlobalProtect Gateways
13.2.3 GlobalProtect App
13.3 Basic Setup Concepts
13.3.1 Create Interfaces and Zones for GlobalProtect
13.4 Enable SSL Between GlobalProtect Components
13.4.1 About GlobalProtect Certificate Deployment
13.4.2 GlobalProtect Certificate Best Practices
14. Panorama
14.1 Panorama Overview
14.2 Panorama Models
14.2.1 Panorama virtual appliance
14.2.2 M-Series appliance
14.3 Centralized Firewall Configuration and Update Management
14.4 Context Switch�XFirewall or Panorama
14.5 Total Configuration Size for Panorama
14.6 Centralized Logging and Reporting
14.7 Log Forwarding Options
14.8 Centralized Reporting
14.9 Forward Logs to Strata Logging Service
15. CN-Series Firewall for Kubernetes
15.1 Overview of CN-Series
15.1.1 Prevent Data Exfiltration from Kubernetes Environments
15.1.2 Prevent Lateral Spread of Threats Across Kubernetes Namespace Boundaries
15.2 CN-Series core concepts
�H�U�C�X�ϥ� PAN-OS �� PA �t�C Next Generation Firewall�G
PA-220R Firewall


PA-400 Series Firewalls

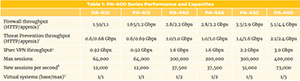
PA-500 Firewall

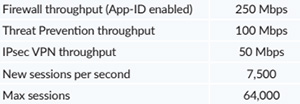
PA-800 Series Firewalls

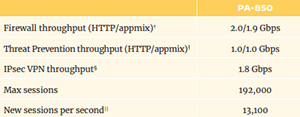
PA-1400 Series Firewalls

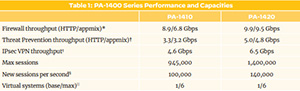
PA-3000 Series Firewalls

PA-3200 Series Firewalls


PA-3400 Series Firewalls

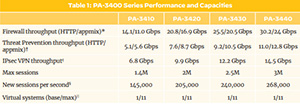
PA-5000 Series Firewalls

PA-5200 Series Firewalls

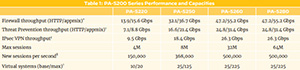
PA-5400 Series Firewalls

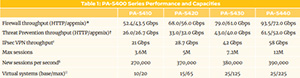
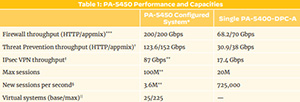
PA-5450 Firewall

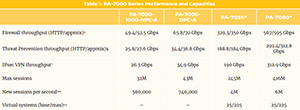
PA-7000 Series Firewalls
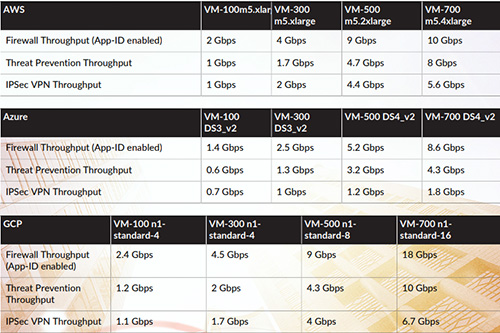
VM (Virtual Machine) Series Firewalls
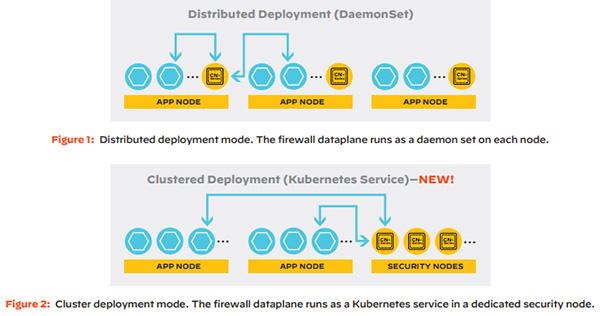
CN (Container) Series Firewall
 �I�ڡC
�I�ڡC