|
Preface
With the recent mass data leaks, encompassing sensitive information such as human resources data, ID card numbers, dates of birth, social media accounts, academic and banking details, as well as health information, there has been a significant damage to the reputation of Asia I.T. Hub – Hong Kong.
Government sectors, enterprises and international communities are expressing heightened concerns regarding the effective storage and security of information, accompanied by proactive defense measures and compliance controls.
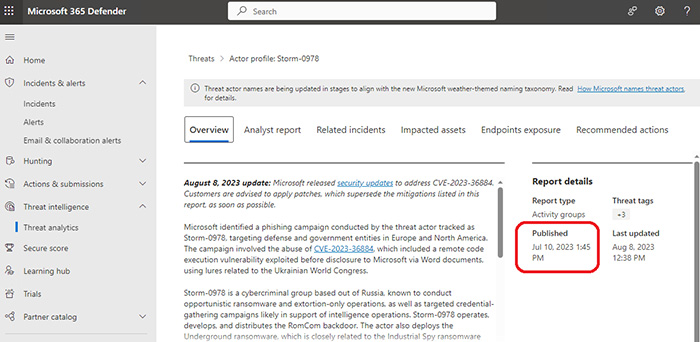
As a leading provider of security services, Microsoft took the initiative by releasing a Threat Intelligence Analyst Report in July 2022. This report presented actionable recommendations to proactively defend against potential cyberattacks.
Microsoft’s approach includes the following key elements:
Threat Intelligence Analyst Reports
These reports are valuable resources for comprehending the evolving threat landscape. They provide insights into emerging threats, attack patterns, and vulnerabilities that organizations should remain vigilant about.
Mitigation Recommendations
Microsoft, along with other security service providers, frequently releases recommendations to mitigate known security risks. These recommendations encompass best practices, system configurations, and the utilization of security tools.
Proactive Defense
Microsoft advocates for proactive cybersecurity measures. This entails the implementation of advanced security solutions such as Microsoft Sentinel, Microsoft 365 Defender, and Defender for Cloud, which offer threat detection, response, and prevention capabilities.
Compliance Controls
Compliance with data protection regulations is of utmost importance. Microsoft offers tools and services to assist organizations in meeting compliance requirements, including GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and others, contingent on their specific industry.
Security Awareness
An essential aspect of Microsoft’s approach is educating users and organizations on cybersecurity best practices. They provide resources and training to empower users to identify and mitigate threats effectively.
Data Encryption and Access Controls
Microsoft underscores the significance of data encryption and stringent access controls to safeguard sensitive information. Azure Key Vault and Microsoft Entra ID (i.e. Azure AD) play pivotal roles in achieving this.
Incident Response
In the event of a security incident or data breach, Microsoft provides guidance on how to respond efficiently. This encompasses containment strategies, investigative procedures, and notification protocols.
It is imperative for organizations not only to rely on the guidance and tools furnished by companies such as Microsoft but also to actively evaluate and bolster their own cybersecurity posture.
This often involves formulating a robust cybersecurity policy, staying abreast of emerging threats, conducting periodic security audits, and continually educating employees on security risks.
In essence, cybersecurity is an ongoing endeavor, and organizations must adapt to the ever-evolving threat landscape to effectively shield their data and preserve their reputation!
As an Information Protection and Compliance administrator, you plan and implement risk and compliance controls in the Microsoft Purview compliance portal.
In this role, you translate an organization’s risk and compliance requirements into technical implementation.
You are responsible for implementing and managing solutions for content classification, data loss prevention (DLP), information protection, data lifecycle management, records management, privacy, risk, and compliance.
You work with other roles that are responsible for governance, data, and security to evaluate and develop policies to address an organization’s risk reduction and compliance goals.
You assist workload administrators, business application owners, human resources departments, and legal stakeholders to implement technology solutions that support the necessary policies and controls.

Microsoft Certified Information Protection and Compliance Administrator Associate
The certification “Microsoft Certified Information Protection and Compliance Administrator Associate” validates your capability to implement security controls and threat protection, protecting data and applications in M365 cloud and hybrid environments as part of end-to-end infrastructure.
About the course
Our training course will guide you through carefully selected examination topics, along with real-life examples, practical demonstration and business cases of implementing, verifying and maintaining various Microsoft 365’s Information Protection and Compliance features.
Evaluations, Pros and Cons and may be comparisons of different Microsoft 365 products would be verbally provided throughout the training course.
As Microsoft has been partnering with multiple 3rd party vendors and built security-related ecosystems, it is inevitable that a small portion of the course time would be spent on briefly discussing popular partner security solutions.
Our senior instructor Mr. Larry Chan would give you advise, tricks and tips on various cloud security-related products.
|

